Get Your Credentials
Introduction
Before making API calls, you need to generate your application credentials. These credentials consist of an API Key and an API Secret, which are linked to the permissions (Domains) set during the application creation process.
Retrieving App Credentials
Step 1
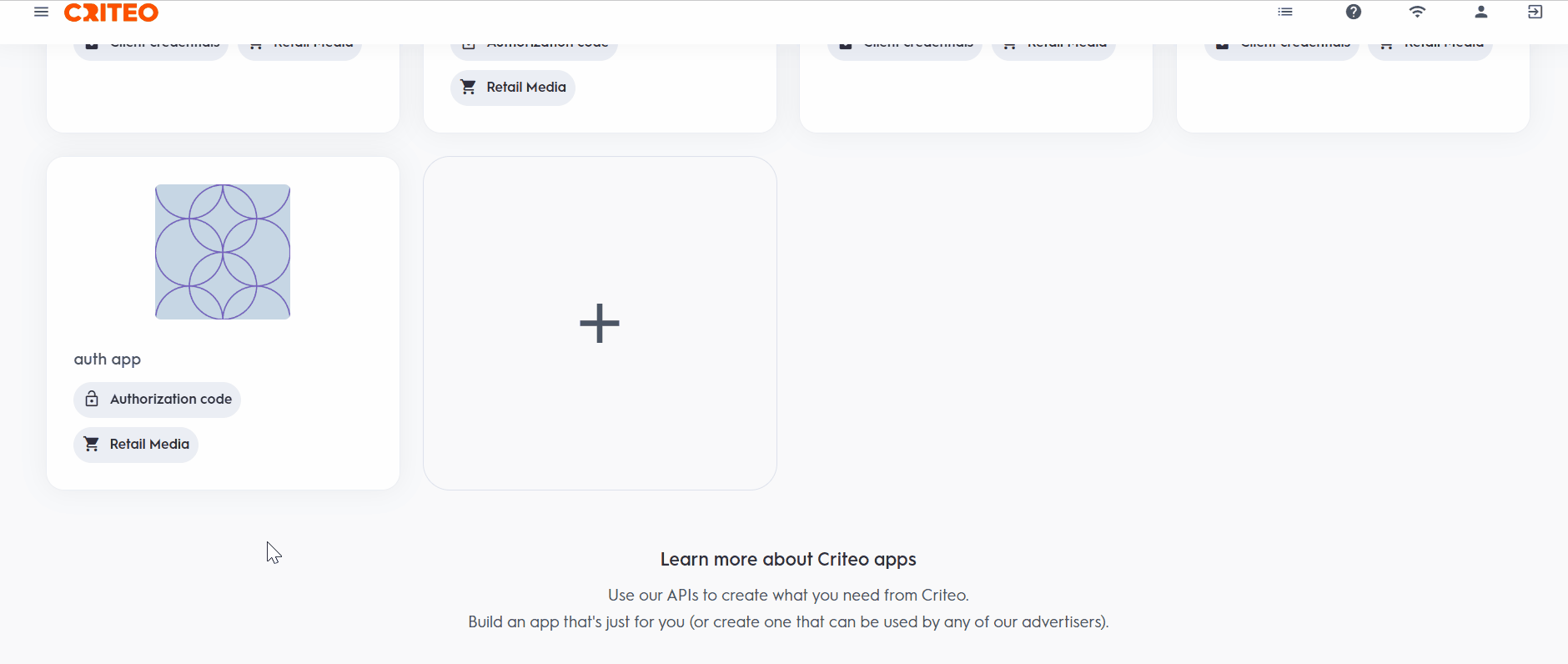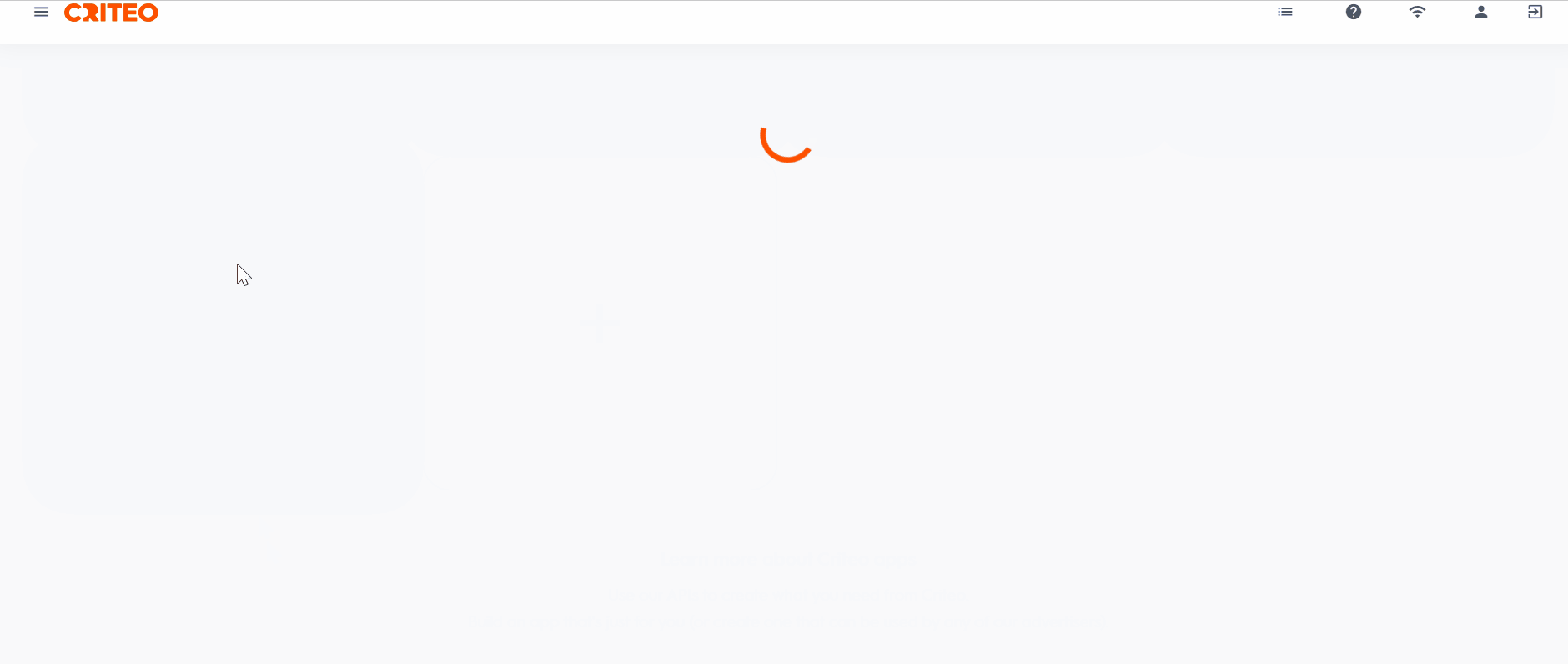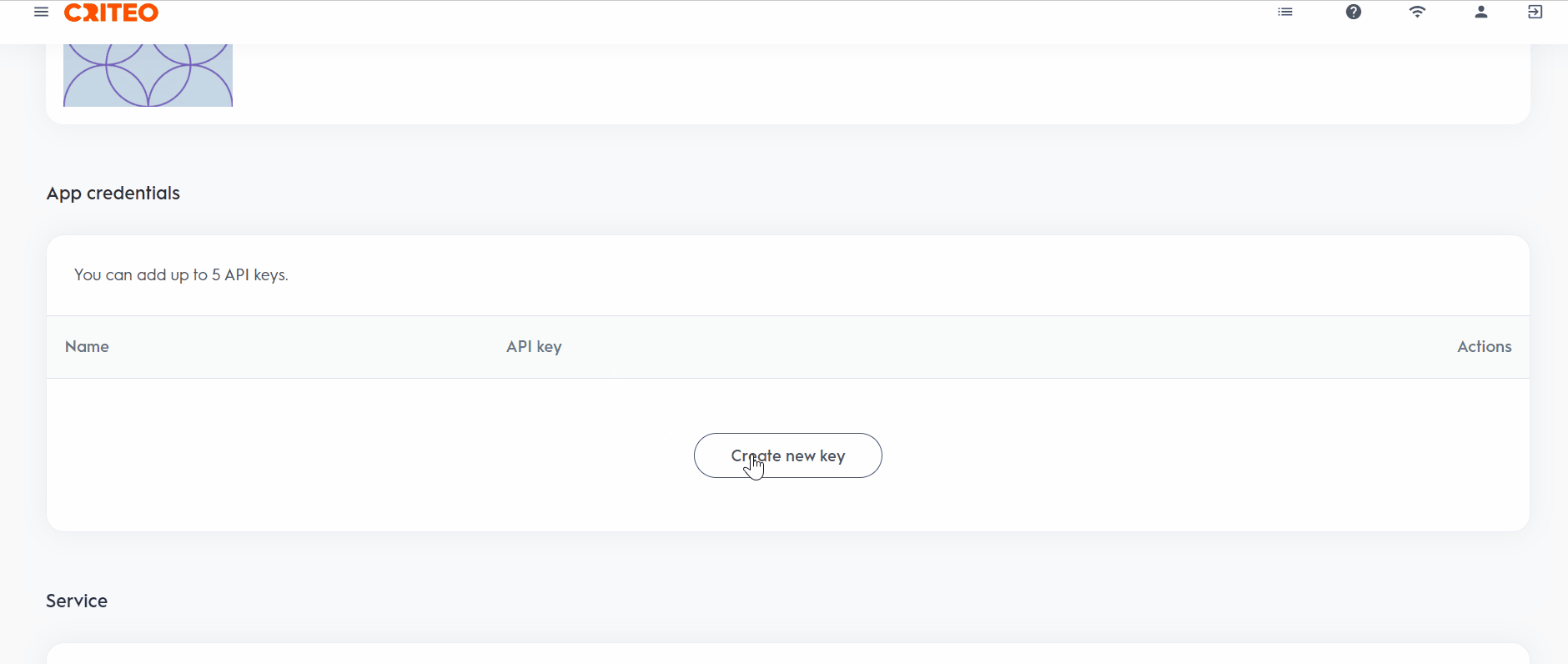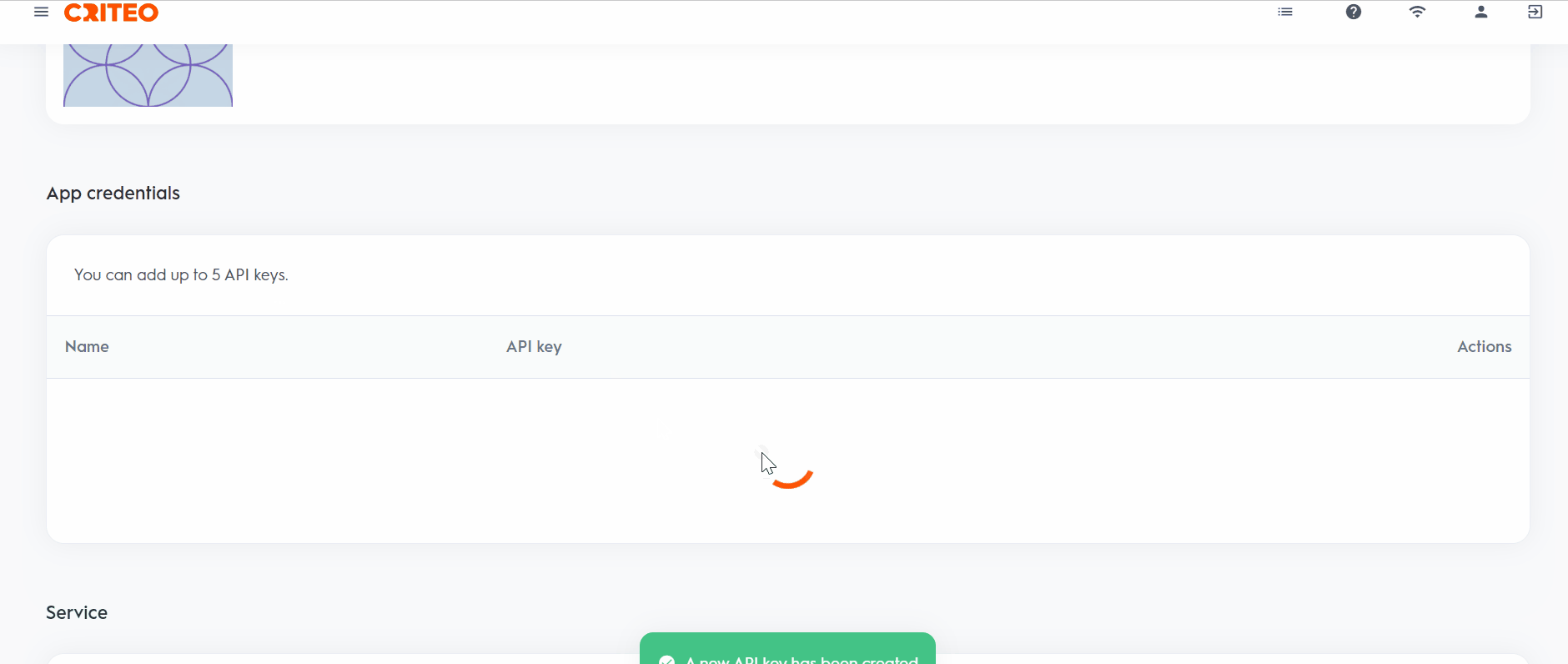
- Log in to the Criteo Partner Dashboard, and from the My Apps page, select the application for which you want to retrieve credentials and click on Create new key to generate your set of credentials.
Step 2
A text file containing both your API Key and API Secret will automatically download.
While you can copy the API Key from the credentials' dashboard, the API Secret is only available in the downloaded file. Make sure to store these keys securely!
Storing API Keys
Your API Secret is only available in the text file. If the file is lost, the API Secret cannot be retrieved, and you will need to create new API keys. So please make sure to store your keys in a safe location! Each application allows up to five keys at a time.
Step 3
With your API credentials in hand, you can call the POST /oauth2/token endpoint to obtain your token.

https://api.criteo.com/oauth2/tokenMore information about the Auth endpoint is available in the API Reference documentation and in our authentication guide.
The steps to obtain the token depend on your selected authentication method: Client Credentials or Authorization Code.
Best Practices
- Use the dashboard to manage your API keys. You can delete a key, and it will remain valid for 15 minutes before deactivating.
- Rename your credentials directly in the dashboard for easy identification, such as "Troubleshooting Credentials" or "Production Credentials."
- You are limited to five API credentials per app, allowing for flexibility (e.g., 1 for production, 1 for troubleshooting, and others for various use cases).
Updated 1 day ago